Explore the cutting-edge research projects in our group
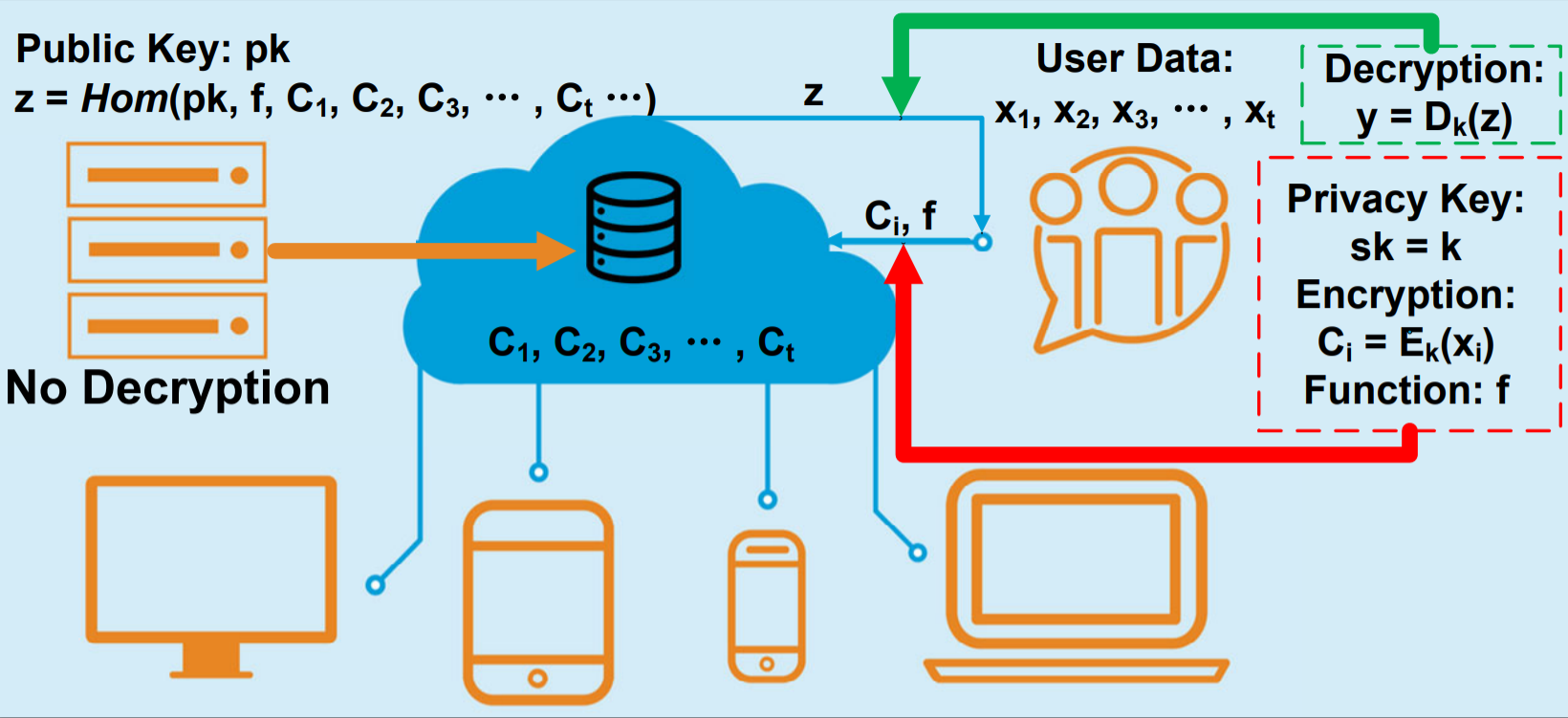
Fully homomorphic encryption (FHE) is an emerging technology that enables an untrusted party (e.g. a cloud server) to perform analytics directly on ciphertexts, while no information of the original plaintext is leaked. However, the current FHE schemes are still computationally-intensive to be applied transparently in real-world applications. Therefore, we are trying to accelerate FHE by co-optimizing its architecture synergically from both algorithm and hardware aspects.
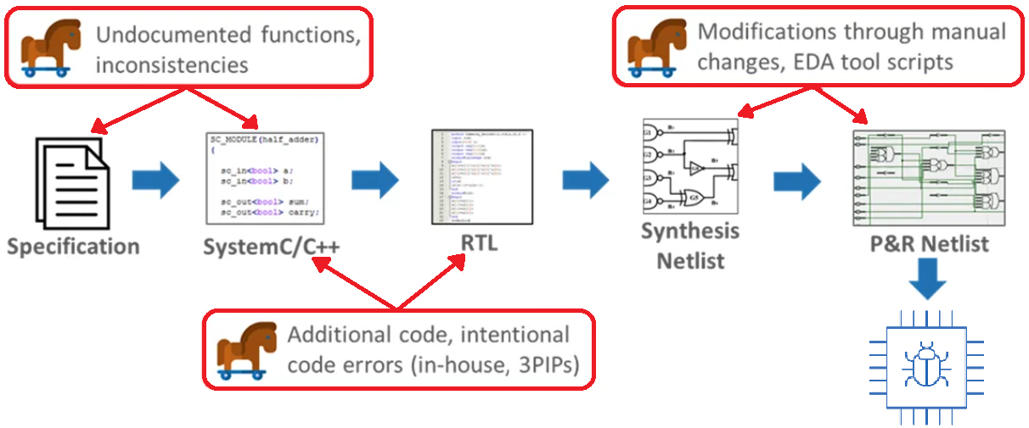
Distributed supply chains make designing application-specific hardware economically feasible. However, adversarial entities can compromise them to maliciously alter the intended design. Our work in machine learning hardware backdoor explores the capabilities of attackers in this setting. This understanding is then used to determine effective defensive measures, and we have extended the threat model into the production phase for the first time.
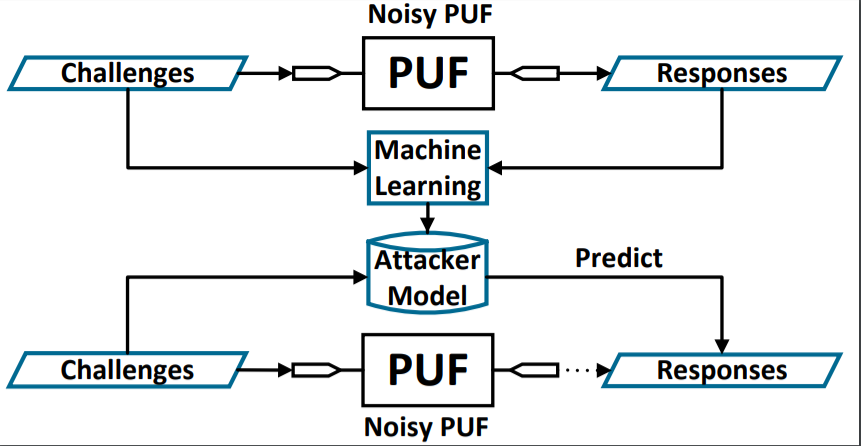
With the rapid development and globalization of the semiconductor industry, hardware security has emerged as a critical concern. New attacking and tampering methods are continuously challenging current hardware protection methods. We are developing novel techniques to improve the performance of physical unclonable functions (PUFs) and hardware obfuscation.
Internet of Things (IoT) sensors often operate in unknown dynamic environments featuring time-sensitive data sources, dynamic processing loads, and communication channels of unknown statistics. This is the natural application domain of reinforcement learning (RL), where optimal decision policies need to be computed/learned online. We seek to develop efficient architectures for overcoming the computational bottlenecks of PDS-based RL.
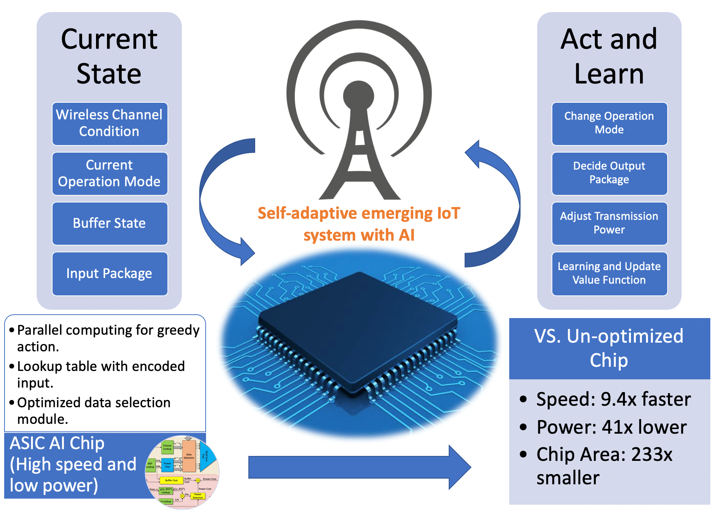
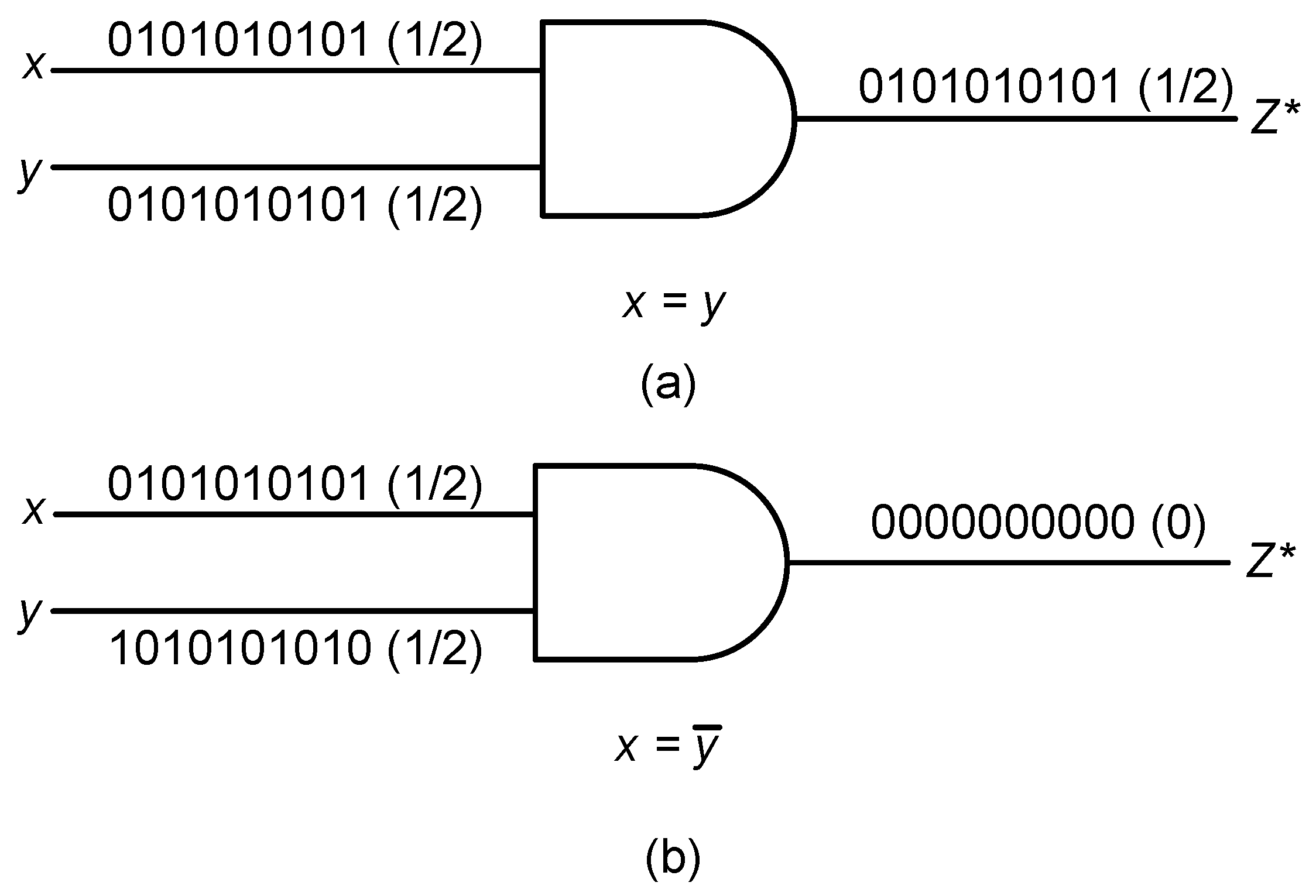
Recently, energy/area-efficient IC design is of great interest given the proliferation of computing devices and the resource-constrained nature of these systems. Stochastic computing has emerged as a promising alternative computing paradigm. We aim to develop efficient hardware architectures for various applications using these emerging techniques.
The learning process of a biological system is a continuous phenomenon with limited external interventions. We are developing methods to accelerate training to achieve a similar pattern as biological learning. These methods are also applicable to online and incremental learning settings.
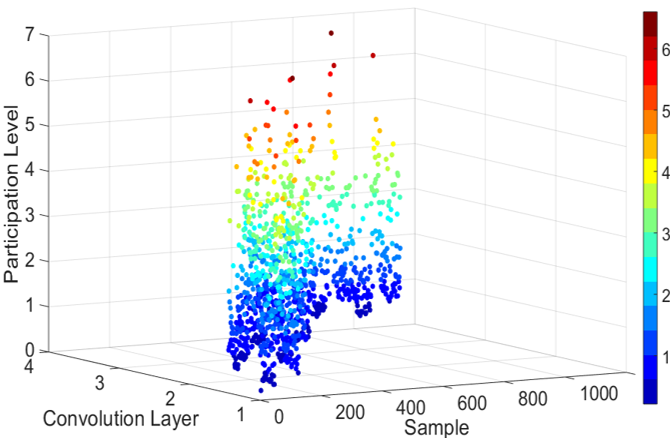
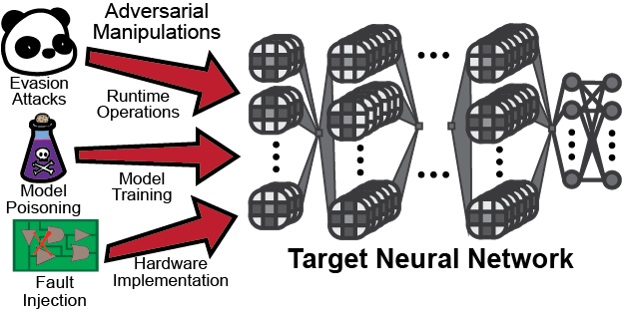
In recent years, deep learning has demonstrated superior performance in various application fields. However, in order to facilitate real-world deployment, security and robustness against attacks have emerged as critical concerns, especially in safety-critical applications. We are investigating adversarial examples, poisoning attacks, and backdoor injection, and developing new attacking methods and countermeasures.